In view of certain threats identified during the information systems audit of Customers Bank Limited (CBL), the auditors have recommended the use of Public Key Infrastructure (PKI).
You are required to write a note to the management explaining the functioning of PKI.
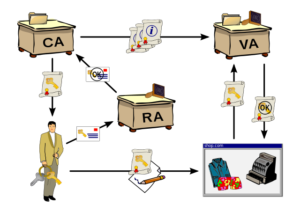
Public Key Infrastructure (PKI)
PKI is a mechanism of encryption and decryption of data using double keys(codes) issued by an independent
trusted third party, known as Certificate Authority (CA). To understand PKI mechanism, consider two users A and B, both having their private and public keys issued by same or different CA.
A can send data to B encrypted by:
(i) his own private key; or
(ii) B’s public key; or
(iii) B’s public key and his own private key.
On receipt of the data, B can decrypt it using:
(i) A’s public key if it is encrypted by A’s private key.
(ii) his own private key if it is encrypted by his own public key.
(iii) his own private key and A’s public key if its encrypted by his own public key and A’s private key.
Share this Public Key Infrastructure (PKI) example with your Class fellow and stay tuned for more updates on this topic please provide feedback on auditorforum. Get more IT practicing questions and answers from our Information Technology session. We are keen to know your views in comments about the situation defined in the question.